Continued Activity targeting the Middle East - PART 2
Update 2017-11-15: Palo Alto's Unit42 released a blog with additional details about the same activity and they are dubbing the group behind this as "MuddyWater".
INTRODUCTION
In an earlier blog post, I wrote about a campaign that was targeting the Middle East (Saudi Arabia, Iraq, UAE, etc). The adversary group behind this campaign seem to have been continuing its activity and advancing its techniques.In this blog I will be sharing some additional details about this adversary group and how they are continuing to evolve. They are still using MS Word documents as lures with embedded Macros and PowerShell scripts however, they have been increasing their obfuscation techniques to make detection harder.
PART 1 - PANDA WAS HERE.
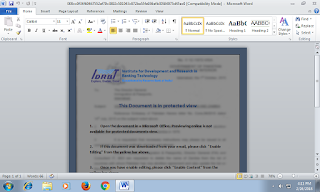
In my previous blog, I mentioned a sample "dollar[.]doc" MD5 a86249a392b394c803ddbd5bbaa0b4bb. While analyzing the sample and looking at some of the strings, one string was interesting "panda was here :)"Using this string to look for additional samples yielded an interesting result. I was able to come across a sample titled "fia.gov[.]pk .doc" MD5 135238bc43fddd0867676aef1e9aaf83. The sample seems to be perpetrating as the Federal Investigation Agency of Pakistan as shown in the picture below:
The Macro code used is very similar to the ones used in the previous campaign that was targeting the Middle East, so I won't be going through the details for that.
I can imagine that using that string alongside some of the meta-data and tags within the doc like the "lastmodifiedby GIGABYTE" could yield additional results and might uncover additional samples.
PART 2 - MORE RECENT SAMPLES AND MORE POWERSHELL SCRIPTS
In the past couple of weeks, I continued to look into this activity and adversary and trying to see if their campaign is continuing or not. Looking at different parts of the Macro code from previous samples and even looking at some of the code from the previous PowerShell scripts. This led me to a sample that was submitted to Hybrid Analysis on October 31, 2017. Interestingly, the sample "mahmut.docx" with MD5 f78bd1a0251e4bef7e86eb4cb14c204d is NOT on VT as the writing of this post.
The Macro code in this document seems to have been modified from the ones that were targeting the Middle East, though similarities still exist as shown below.
 |
| GSB.doc vs Mahmut.docx |
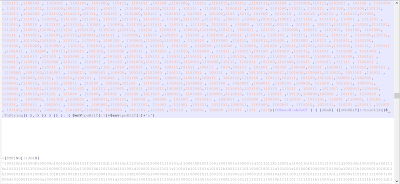
The heavy reliance on the use of Base64 encoding is still there to encode both the Powershell script and the VBS script. The encoded Powershell scripts looks something like this
As you can see, the encoded Base64 is split and will be added at the later stage and decoded. Once you decode the Base64 code, you will be presented by a PowerShell script that looks something like this
The outcome is still obfuscated with the same obfuscation technique used in the "dollar.doc" and "fia.gov.pk .doc". Cleaning this up, you will be presented with something like this
MORE OBFUSCATION!!! This time, there is plenty of junk code spread across and need to be cleaned up and properly replaced with the right tags. This will looks like this
This is somewhat better but as we can see there is still another layer of obfuscation in the form of array manipulation. However, you can clearly find the interesting tags like "IP, ID, cS, localMachine, K and Proxy". Interestingly, the variable K has the value of "BitDefender". One thing to highlight is that this adversary is still using the same IP from the previous campaign for their C&C 148.251.204[.]131:8060/
Looking at the Proxy variable and cleaning that up, we will be presented with the following list of Proxy sites. This time the list seem to have grown to over 50 URLs. I am including the full list at the end of the blog post.
While analyzing the PowerShell script I was able to come across additional samples that has striking similarities to this one, I am also adding the hashes for these at the end.
PART 3 - MORE POWERSHELL
The PowerShell script had a second part which was also obfuscated with similar technique as shown below
Cleaning this up and de-obfuscating it will present us with the code that shows how this adversary is interacting with victim machines. Looking at the code, it seems that it is still using similar functions and methods as the previous campaign (getKey, Register, httpSend, httpGet, getCommand, sendResult, persist and isDeugEnv). Notice that there is a function that is checking for debuggers and analysis tools "isDeugEnv" and it is even misspelled which makes me think that they attackers modified this intentionally since some controls look for "isDebugEnv".
Cleaning this up and de-obfuscating it will present us with the code that shows how this adversary is interacting with victim machines. Looking at the code, it seems that it is still using similar functions and methods as the previous campaign (getKey, Register, httpSend, httpGet, getCommand, sendResult, persist and isDeugEnv). Notice that there is a function that is checking for debuggers and analysis tools "isDeugEnv" and it is even misspelled which makes me think that they attackers modified this intentionally since some controls look for "isDebugEnv".
CONCLUSION
The Adversary Group behind this campaign seems to be continuing its activities and focusing on reconnaissance and information gathering at this stage. Although there is no clear evidence that this campaign was targeting a specific region or country, the lure documents might indicate that the campaign is focused on Middle East and Pakistan region as it is also shows in the Proxy sites.
This blog is probably scratching the surface of the overall campaign and activities by this adversary and it would be interesting to see how they continue to develop and what their end goal would be.
This blog is probably scratching the surface of the overall campaign and activities by this adversary and it would be interesting to see how they continue to develop and what their end goal would be.
IoCs
LURE DOCUMENTS
dollar[.]doc - a86249a392b394c803ddbd5bbaa0b4bb
fia.gov[.]pk [.]doc - 135238bc43fddd0867676aef1e9aaf83
mahmut[.]docx - f78bd1a0251e4bef7e86eb4cb14c204d
fia.gov[.]pk [.]doc - 135238bc43fddd0867676aef1e9aaf83
mahmut[.]docx - f78bd1a0251e4bef7e86eb4cb14c204d
PowerShell Scripts - SHA256
16937e76db6d88ed0420ee87317424af2d4e19117fe12d1364fee35aa2fadb75
d42aa9cc8812beb0c8d0344195319884a794ab354d374fcddb81ec58d9d32e3c
795f2aa25f19670334c2d9ead72ab210849ea6242873760a3beb561c044eccec
335b05f50f859c84e0de73c78ca5b2c0f35f808500eaff521a348e451b7c6702
e0c7f7a71a58bf51dc04c58212fc320e1a7f2eb74700ed1a928f5960e83683e7
cda1f9b6066f940a0f0e49e76cd2ea90081360348f7005a98d37574233e78d15
dffa36bcca4e1e29533d7f10ab41130808d518353ce3368c96fede7b75059030
d2fdd7af2eabd248fd9a1dc876aa8fb73e7c0cc4a9fda77cd5eb5f7a2784032f
d42aa9cc8812beb0c8d0344195319884a794ab354d374fcddb81ec58d9d32e3c
795f2aa25f19670334c2d9ead72ab210849ea6242873760a3beb561c044eccec
335b05f50f859c84e0de73c78ca5b2c0f35f808500eaff521a348e451b7c6702
e0c7f7a71a58bf51dc04c58212fc320e1a7f2eb74700ed1a928f5960e83683e7
cda1f9b6066f940a0f0e49e76cd2ea90081360348f7005a98d37574233e78d15
dffa36bcca4e1e29533d7f10ab41130808d518353ce3368c96fede7b75059030
d2fdd7af2eabd248fd9a1dc876aa8fb73e7c0cc4a9fda77cd5eb5f7a2784032f
PROXY SITES
hxxp://diplomat[[.]]com[[.]]sa/wp-content/plugins/wordpress-importer/cache[.]php?c=
hxxp://www[.]vanessajackson[[.]]co[[.]]uk/work[.]php?c=
hxxps://www[.]spearhead-training[[.]]com/work[.]php?c=
hxxp://www[.]nigelwhitfield[[.]]com/v2/work[.]php?c=
hxxps://www[.]spearhead-training[[.]]com//html/power[.]php?c=
hxxp://www[.]elev8tor[[.]]com/show-work[.]php?c=
hxxp://watyan[.]nfe[[.]]go[[.]]th/e-office/lib/work[.]php?c=
hxxp://mainandstrand[[.]]com/work[.]php?c=
hxxp://watyanagr[.]nfe[.]go[[.]]th/watyanagr/power[.]php?c=
hxxp://www[.]jdarchs[[.]]com/work[.]php?c=
hxxp://www[.]akhtaredanesh[.]com/d/file/sym/work[.]php?c=
hxxp://106[.]187[.]38[.]21/short_qr/work[.]php?c=
hxxp://www[.]akhtaredanesh[.]com/d/oschool/power[.]php?c=
hxxp://www[.]arcadecreative[.]com/work[.]php?c=
hxxp://cbpexbrasilia[.]com[.]br/wp-includes/widgets/work[.]php?c=
hxxp://whiver[.]in/power[.]php?c=
hxxp://cbpexbrasilia[.]com[.]br/wp-content/plugins/wordpress-seo/power[.]php?c=
hxxp://feribschat[.]eu/logs[.]php?c=
hxxp://azmwn[.]suliparwarda[.]com/wp-content/plugins/wpdatatables/panda[.]php?c=
hxxp://www[.]armaholic[.]com/list[.]php?c=
hxxp://azmwn[.]suliparwarda[.]com/wp-content/themes/twentyfifteen/logs[.]php?c=
hxxp://www[.]eapa[.]org/asphalt[.]php?c=
hxxp://suliparwarda[.]com/wp-content/plugins/entry-views/work[.]php?c=
hxxp://www[.]shapingtomorrowsworld[.]org/category[.]php?c=
hxxp://suliparwarda[.]com/wp-content/themes/twentyfifteen/work[.]php?c=
hxxp://bangortalk[.]org[.]uk/speakers[.]php?c=
hxxps://wallpapercase[.]com/wp-includes/customize/logs[.]php?c=
hxxp://www[.]ridefox[.]com/content[.]php?c=
hxxps://wallpapercase[.]com/wp-content/themes/twentyfifteen/logs[.]php?c=
hxxps://coa[.]inducks[.]org/publication[.]php?c=
hxxp://www[.]yaran[.]co//wp-content/plugins/so-masonry/logs[.]php?c=
hxxp://www[.]dafc[.]co[.]uk/news[.]php?c=
hxxp://www[.]yaran[.]co/wp-includes/widgets/logs[.]php?c=
hxxps://mhtevents[.]com/account[.]php?c=
hxxp://www[.]asan-max[.]com/files/articles/css[.]aspx?c=
hxxp://best2[.]thebestconference[.]org/ccb/browse_cat[.]php?c=
hxxp://www[.]asan-max[.]com/files/articles/large/css[.]aspx?c=
hxxp://www[.]mitegen[.]com/mic_catalog[.]php?c=
hxxp://magical-energy[.]com/css/css[.]aspx?c=
hxxp://www[.]pomegranates[.]org/index[.]php?c=
hxxp://magical-energy[.]com/css[.]aspx?c=
hxxp://www[.]autotrans[.]hr/index[.]php?c=
hxxp://riyadhfoods[.]com/css/edu[.]aspx?c=
hxxps://skepticalscience[.]com/graphics[.]php?c=
hxxp://riyadhfoods[.]com/jquery-ui/js/jquery[.]aspx?c=
hxxp://tmclub[.]eu/clubdata[.]php?c=
hxxp://www[.]kunkrooann[.]com/inc/work[.]php?c=
hxxp://www[.]ztm[.]waw[.]pl/pop[.]php?c=
hxxp://school[.]suliparwarda[.]com/components/com_akeeba/work[.]php?c=
hxxp://www[.]mackellarscreenworks[.]com/work[.]php?c=
hxxp://school[.]suliparwarda[.]com/plugins/editors/codemirror/work[.]php?c=
hxxp://www[.]arcadecreative[.]com/work[.]php?c=
C&C
148.251[.]204[.]131:8060/










Comments
Post a Comment